Introduction#
Recently, I have been responsible for managing code repositories and conducting code reviews for a portion of the company's projects. I have been using SonarQube, a code quality inspection tool, which, when integrated with GitLab CI, can automatically perform code quality checks and generate inspection reports upon each merge request/commit.
This article documents the entire process of importing a project into GitLab repository for configuration, so that it can serve as a reference for configuring other projects.
SonarQube Project Configuration#
Project Dashboard#
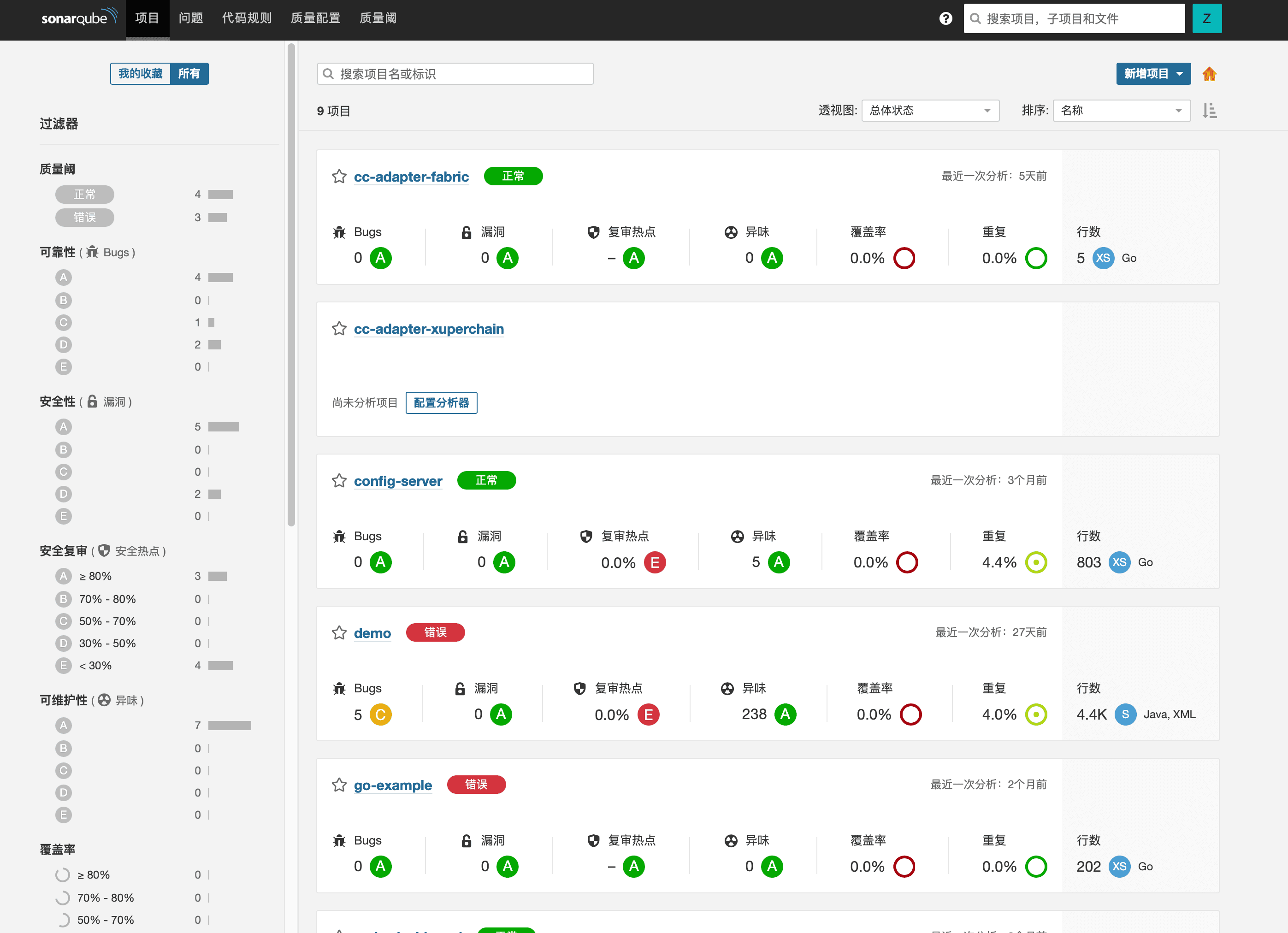
The SonarQube project dashboard, as shown in the above image, provides an analysis of the project's code quality in the form of ratings. After each code analysis, it is possible to intuitively analyze the code from multiple dimensions. Before merging branches, the submitter can refer to the analysis results to make necessary modifications to the code, reducing the unnecessary workload for code reviewers.
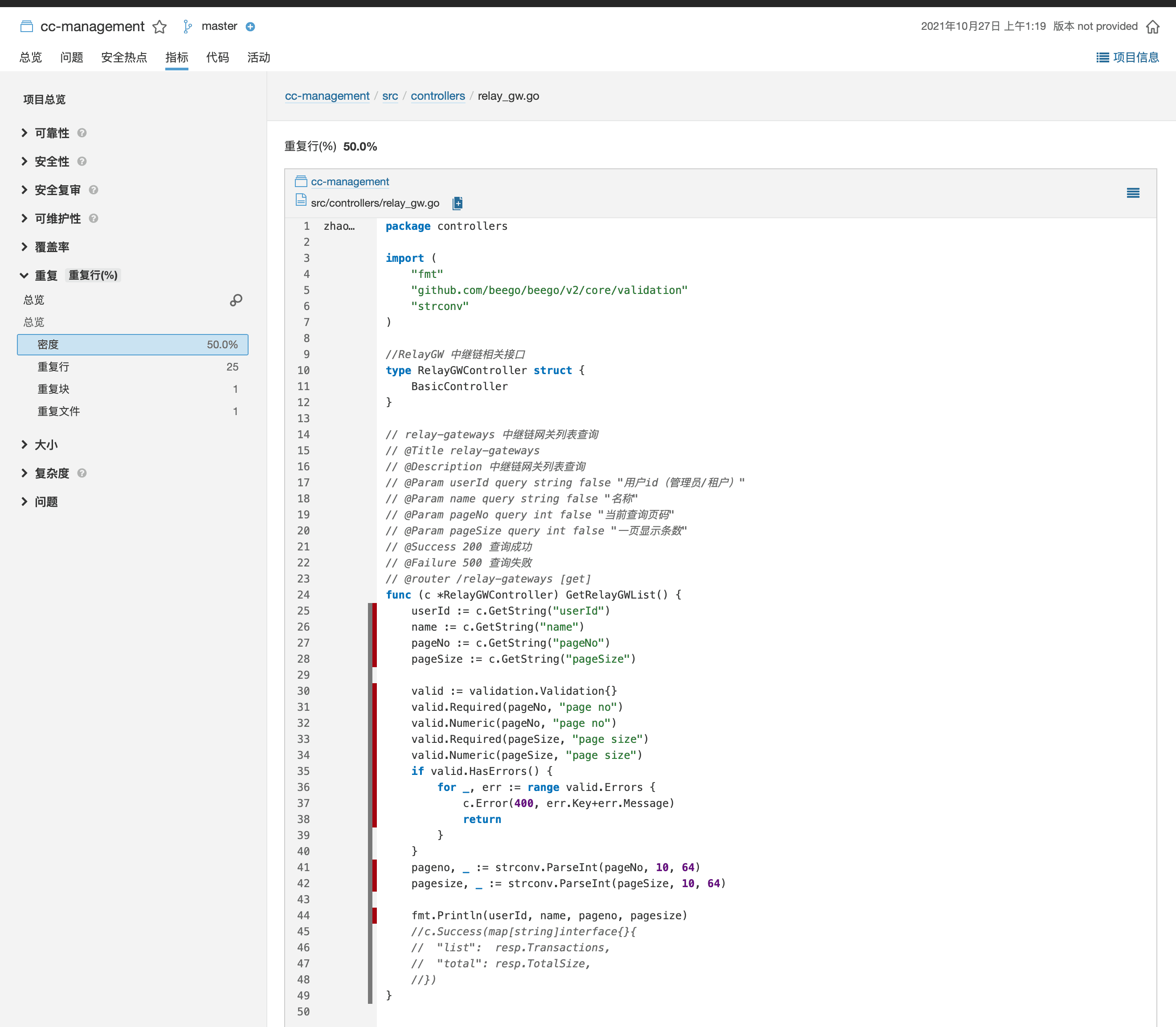
Clicking on specific metrics allows for a detailed examination of the identified issues in the code files, providing a valuable reference for manual code reviews.
Project Configuration#
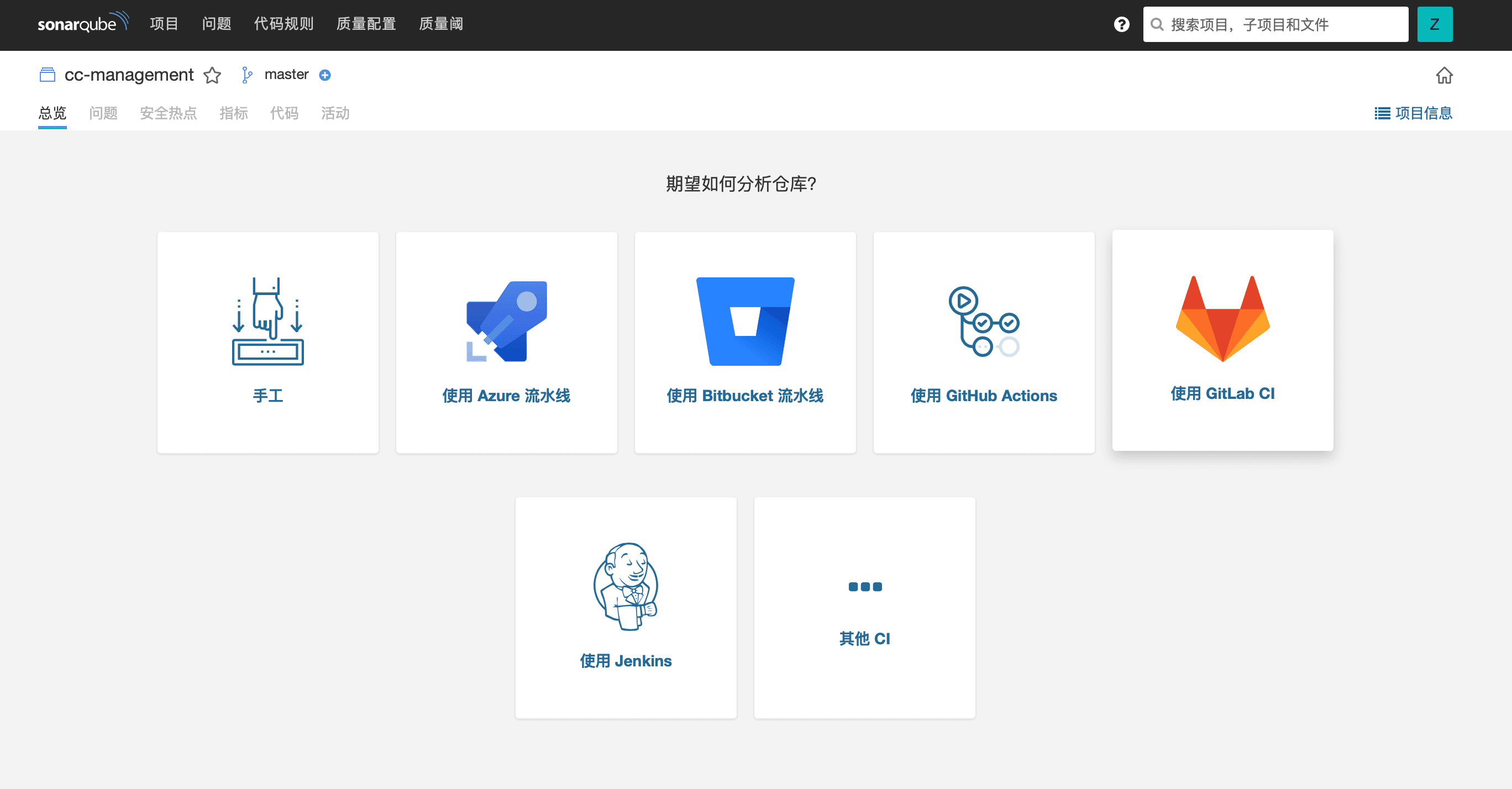
Clicking on "New Project" in the upper right corner allows for the selection of different analysis methods. It supports commonly used code repository automation workflows such as Jenkins, GitLab CI, and GitHub Actions. This article will primarily explain the configuration method for GitLab CI.
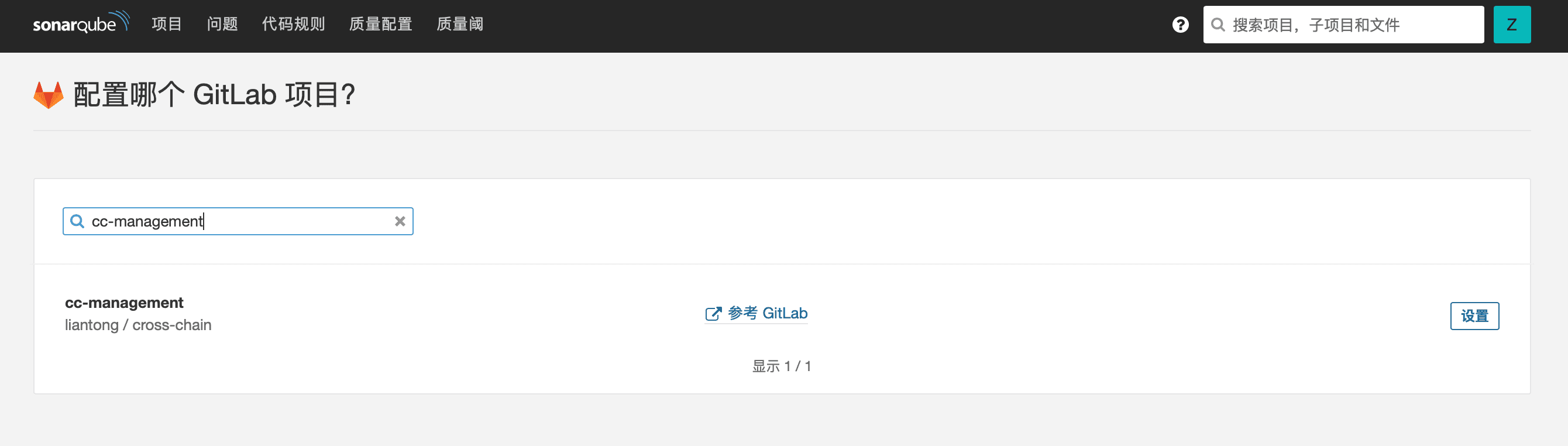
After selecting GitLab CI, choose the project repository associated with the GitLab account for subsequent configuration.
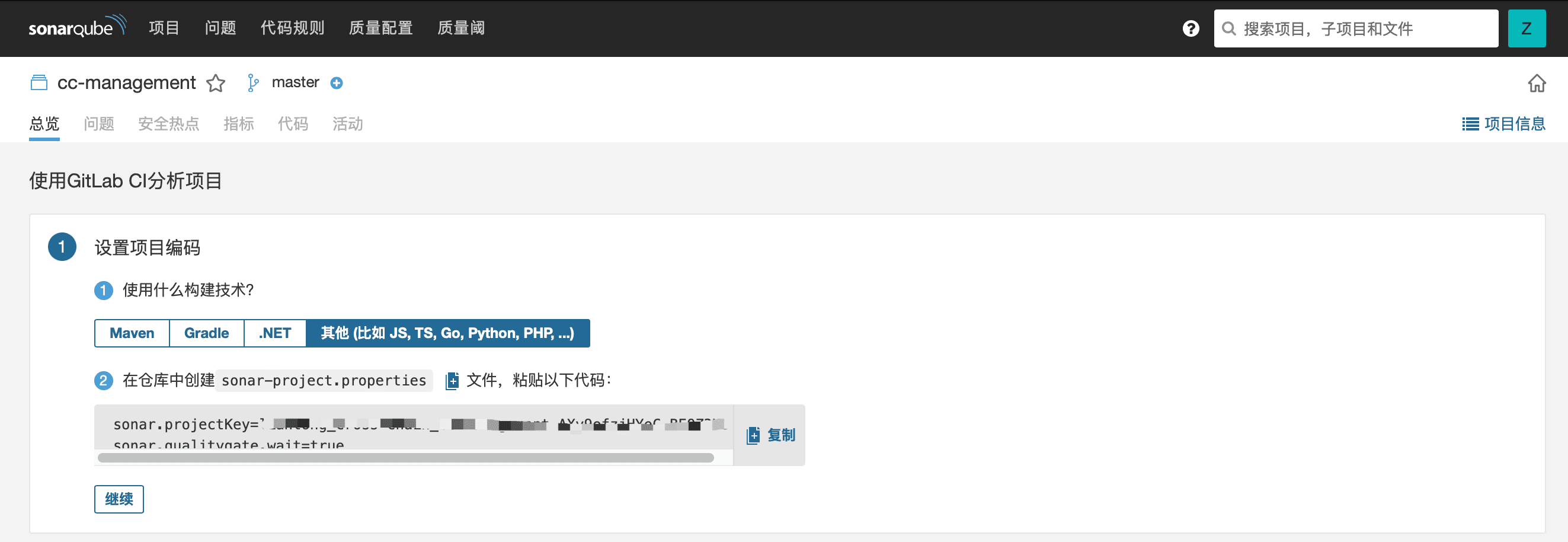
Taking a Go project as an example, first, we need to manually create a sonar-project.properties file and paste the configuration information as prompted.

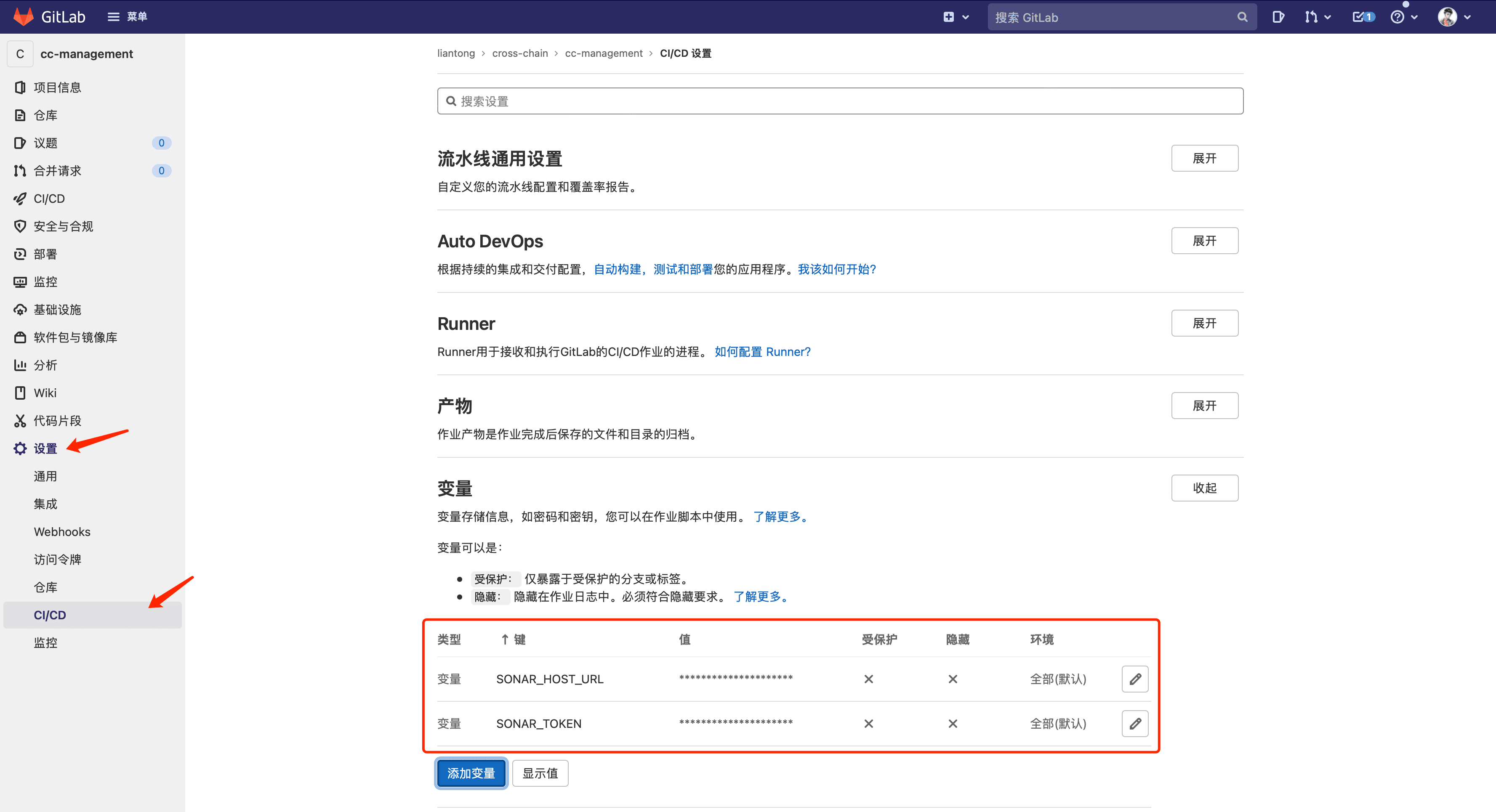
Then, a token needs to be created for the project and the token and URL variable values should be entered in GitLab under "Settings" - "CI/CD" - "Variables".
CI Configuration#
After completing the basic project configuration, it is necessary to configure the GitLab CI workflow through .gitlab-ci.yml. My configuration is shown in the following image:
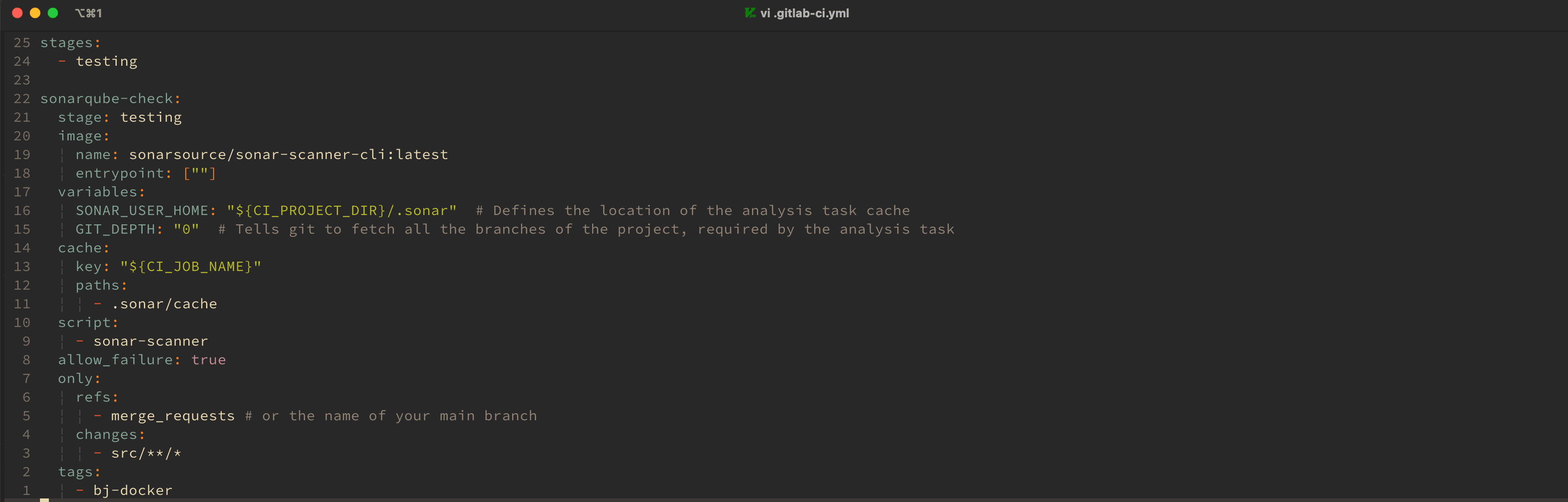
I mainly set it up so that when a merge request is made to the repository and there are changes in the code under the src directory, the testing pipeline is executed to perform code quality checks using SonarQube.
Additional scripts, such as deployment, can be added in GitLab CI to optimize the workflow in conjunction with the SonarQube tool. The project's CI script needs to add the corresponding Runner for execution.
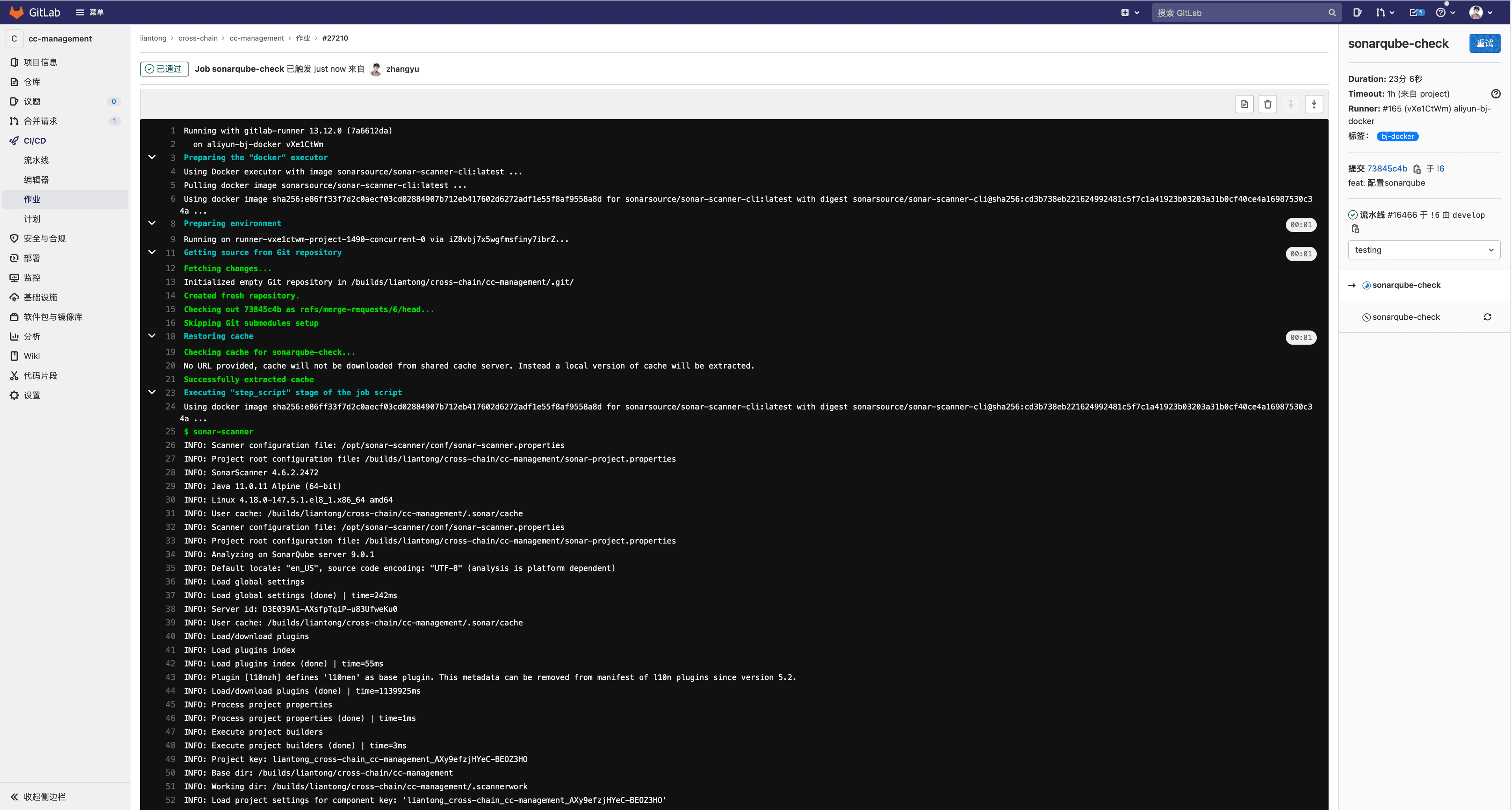
When a merge request is detected, sonarqube-check is triggered for execution, and the final execution result is returned.
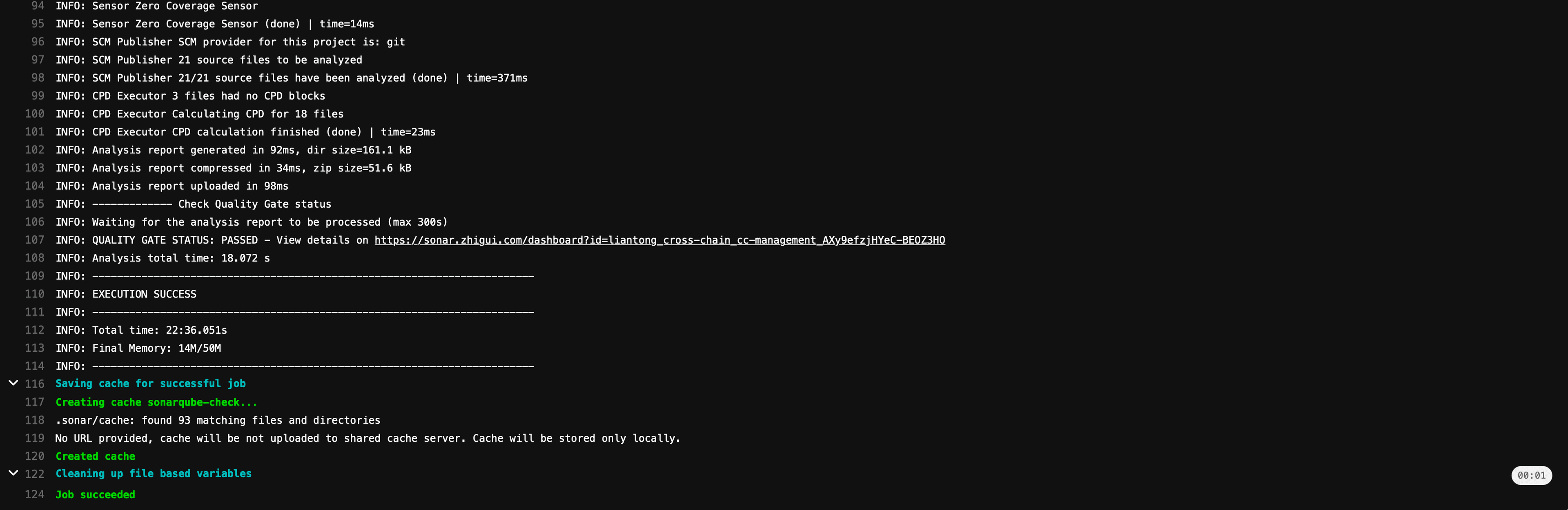
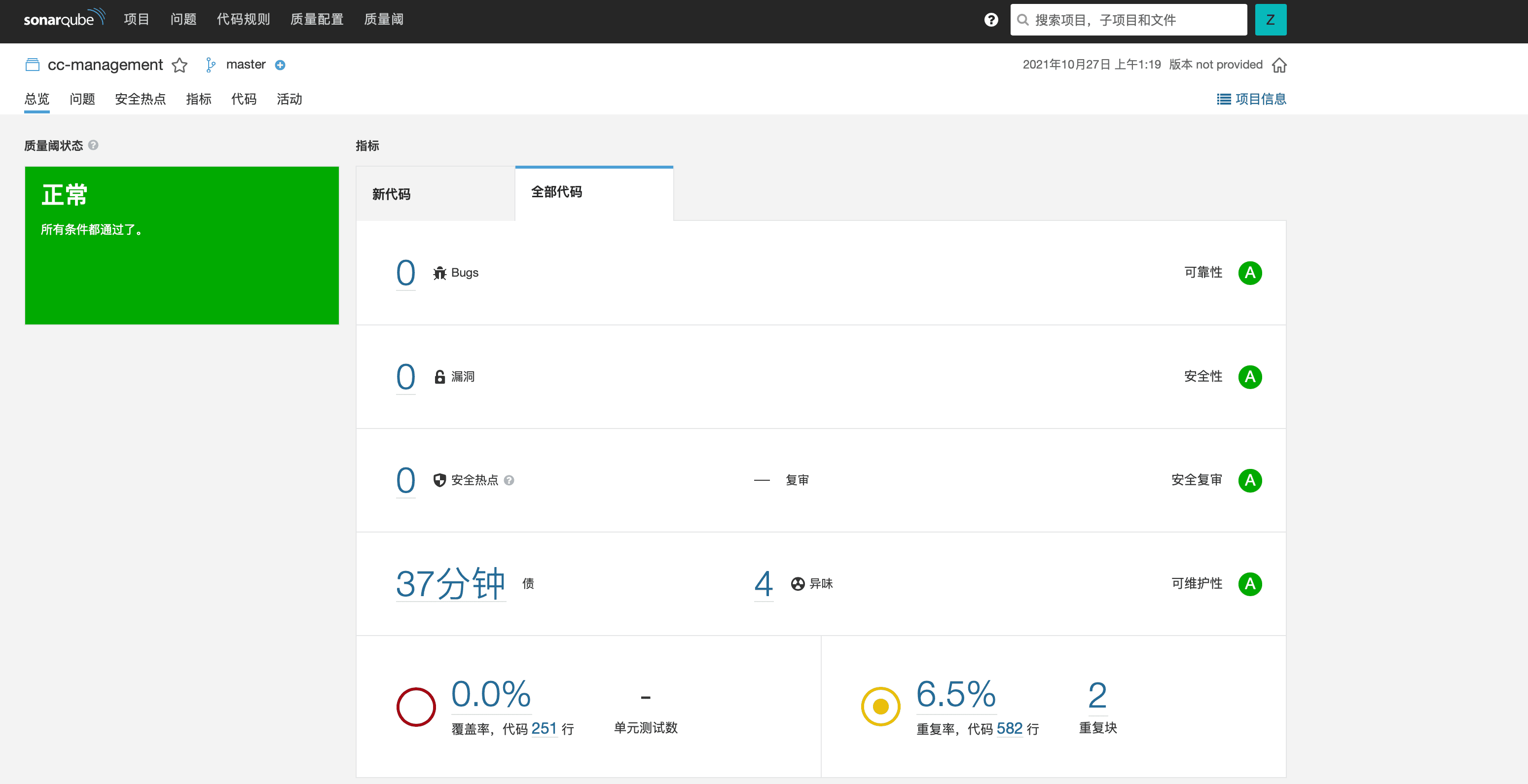
At this point, when the project page in SonarQube is opened, analysis information is already available, indicating the completion of the code quality check for this iteration.
Conclusion#
The above is the complete process of configuring the SonarQube code quality inspection tool for a Go project in a GitLab repository. Automated code quality checks are an important part of the development and operations standard process, especially in team projects. Good standards help optimize workflows and improve the overall quality of projects.
In the future, I will also document the configuration and usage of open-source tools used in development and operations standards in my work. If there are any errors or omissions, please feel free to provide feedback.